AWS networking allows creating fast, reliable and secure network. AWS offers many services like Amazon VPC, Amazon EC2, Amazon Route 53, Load balancers, Amazon gateway and more. Using these services we can make underlying infrastructure.
In this article we are going to discuss about AWS networking services.
AWS Networking services
Regions – AWS data centers are located across globe in Europe, America and Asia. These center locations are called as regions.
Availability zones – These are isolated data centers in regions. We can deploy applications and databases across multiple availability zone. So that if one AZ goes down, user requests are routed to another AZ.
This picture illustrates regions and availability zones.
Three regions (N. California, Oregon, GovCloud)
Three data centers in N. California: us-west-1a, us-west-1b, us-west-1c

- VPN (Virtual Private Network) - A VPN or Virtual Private Network creates a private network connection between devices through the internet. VPNs are used to safely and anonymously transmit data over public networks. They work by masking user IP addresses and encrypting data so it's unreadable by anyone not authorized to receive it.

- VPC (Virtual Private Cloud) – It provides logical isolation to cloud resources. The VPC has one subnet in each of the Availability Zones in the Region, EC2 instances in each subnet, and an internet gateway to allow communication between the resources in your VPC and the internet. When you create your AWS account, we create a default VPC in each Region. A default VPC is a VPC that is already configured and ready for you to use. For example, there is a default subnet for each Availability Zone in each default VPC, an internet gateway attached to the VPC, and there's a route in the main route table that sends all traffic (0.0.0.0/0) to the internet gateway. Alternatively, you can create your own VPC and configure it to meet your needs.
Components of a VPC
A Virtual Private Cloud: A logically isolated virtual network in the AWS cloud. You define a VPC’s IP address space from ranges you select.
Subnet: A segment of a VPC’s IP address range where you can place groups of isolated resources (maps to an AZ, 1:1).
Internet Gateway: The Amazon VPC side of a connection to the public Internet.
NAT Gateway: A highly available, managed Network Address Translation (NAT) service for your resources in a private subnet to access the Internet.
Route tables – Here we will define each route to reach destination. We associate it with subnet. And there is route in the main route table that sends all traffic (0.0.0.0/0) to the internet gateway.
Types of Route:
Main - This is default route table. This is created automatically when VPC is created.
Secondary - User created custom route table. Using this private subnet can communicate with outside world.
Load Balancers – Load balancing automatically distributes traffic across multiple targets such as EC2 instances, in multiple availability zones. This increases availability of application.
Security Groups – It is stateful virtual firewall that controls inbound and outbound network traffic to AWS resources and AWS EC2 instances and are launched with security groups.
Elastic network interfaces – It is a virtual network interface that you can attach to an instance in a VPC. Elastic network interfaces are only available within a VPC and are associated with a subnet upon creation.
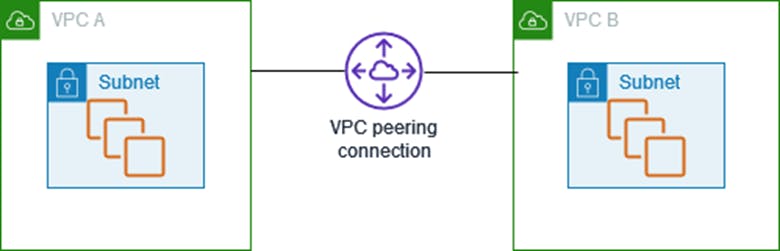
- VPC peering - A VPC peering connection is a networking connection between two VPCs that enables you to route traffic between them using private IPv4 addresses or IPv6 addresses. Instances in either VPC can communicate with each other as if they are within the same network. You can create a VPC peering connection between your own VPCs, or with a VPC in another AWS account. The VPCs can be in different Regions (also known as an inter-Region VPC peering connection).
AWS Networking Hands on
Hands on VPN configuration
a. Create Ec2 instance, install OpenVPN and configure it - Launch Ec2 instance, browse for more AMIs and select OpenVPN access server.

b. Select instance type as t2-micro, create new key pair and click on launch instance. Select all options for VPN configuration as default. After successful configuration EC2 console will return Admin UI and Client UI URL. Copy that URL and Login using username and password.
Admin UI : https://13.201.102.9:943/admin
Client UI : https://13.201.102.9:943/
c. Configure OpenVPN and setup route (all Ec2 instance are accessible via VPN) –
d. Login with username and password to OpenVPN console using admin UI (13.201.102.9:943/admin).
e. Go to VPN Settings and change VPN settings.

f. Go to User management. Setup user in OpenVPN server and enable auto login. Download user profile.

g. Login to Client UI (https://13.201.102.9:943/) and download OpenVPN connect. Install and Go to OpenVPN connect. Import profile which we created and downloaded. Click on Connect

h. Create Linux EC2 instance and Access Ec2 instance via private address. Go to Linux Server Security groups and modify inbound rule for OpenVPN server private IP address.

i. Now we cannot connect Linux Server EC2 instance using public IP, instead we connect it using private ip

Hands on VPC
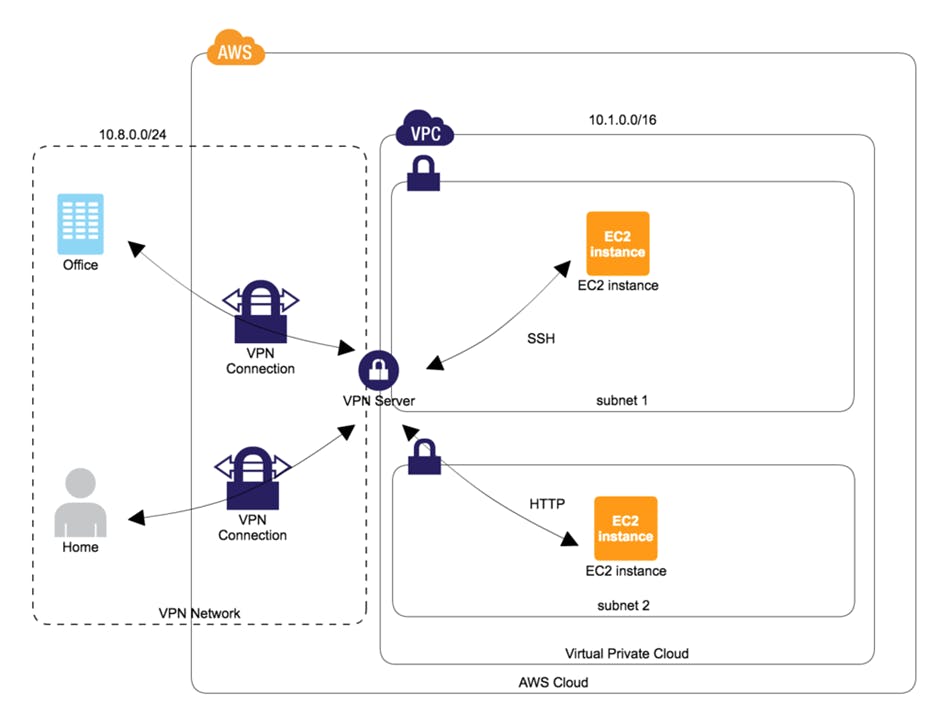
Requirement – We want to login into public ec2 instance and from public ec2 instance we will login into private ec2 instance and ping google.com. So that we can communicate with private subnet from outside world.
Image below shows what we want to achieve.

a. Create VPC

This will create a public route table

b. Create public subnet – Create public and private subnet for custom VPC.



c. Create Internet Gateway – Create internet gateway and attach it to VPC.

d. Create Secondary Route Tables as pvt-rt and make it private route tables associate private subnet

e. Rename main Route table as pub-rt and associate it with public subnet.

f. Associate private route table with private subnet.

g. Launch public EC2 instance – Create pub-ec2 with below network settings.

h. Launch Private EC2 instance – Create pvt-ec2 with below network settings.

i. Edit Route table to communicate from outside VPC.

j. Create NAT Gateway – Create NAT gateway in public subnet with allocating elastic IP.

k. Create route for private subnet –

l. Login public EC2 instance(from public ec2 instance login to private ec2 instance and ping google.com)
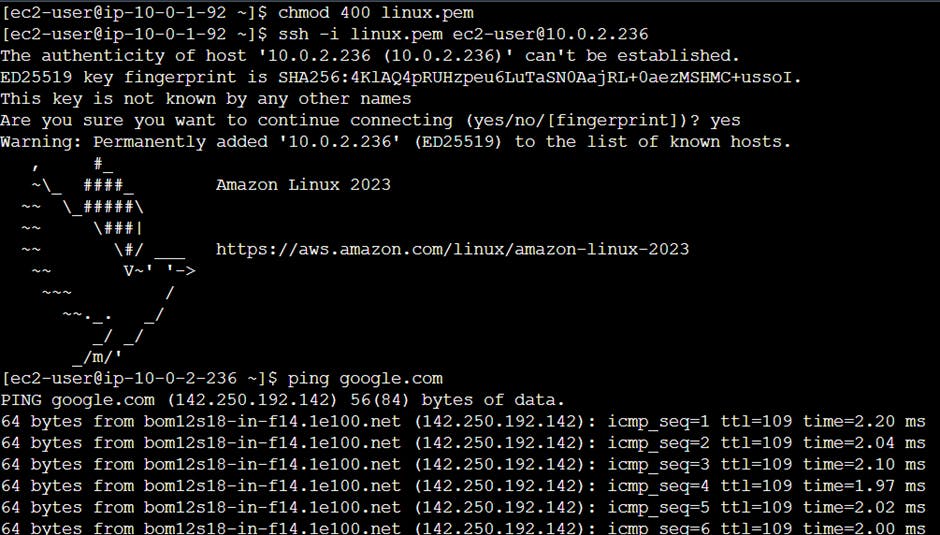
Hands on VPC peering
a. Create another VPC in different region(North Virginia).

b. Create subnet


c. Create route table and associate it with subnet

d. Create private EC2 instance

e. Create VPC peering connection for VPC in Mumbai region

f. Accept peering request in N.Virginia region.

g. Add route for peering connection in route table in Mumbai and N.Virginia region


h. Create route for peering connection in route table in N.Virginia region
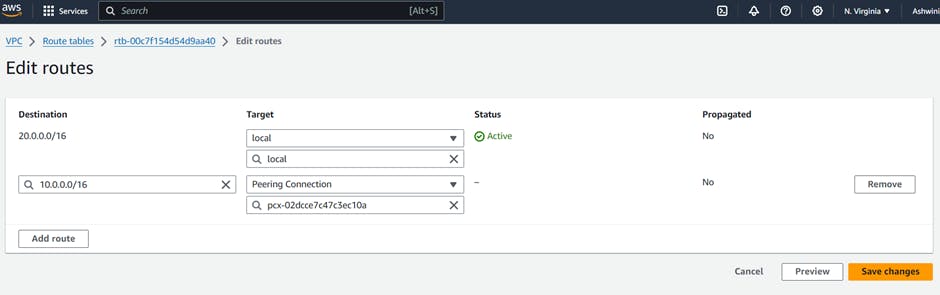
i. Connect N.Virginia region EC2 instance from Mumbai region EC2 instance. So that we can connect from 10 network to 20 network.